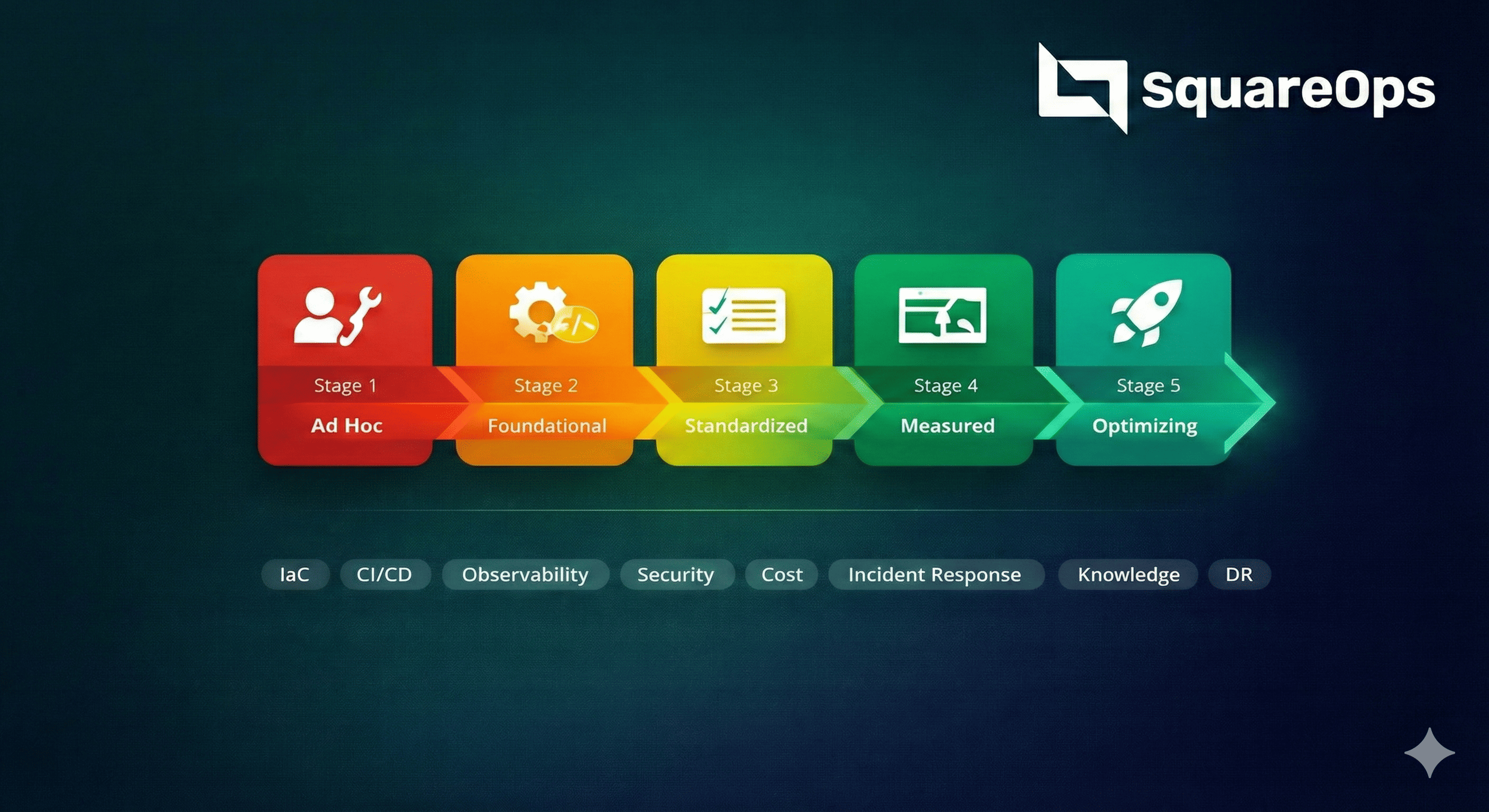
What is an Infrastructure Audit?
An infrastructure audit is a systematic evaluation of your cloud environment to assess its security posture, operational efficiency, cost effectiveness, and compliance status. It provides a comprehensive view of your current state and identifies gaps between where you are and where you need to be.
Unlike automated scanning tools that produce generic reports, our audits combine automated assessment tools with expert human analysis. Our certified architects review your architecture holistically, understanding your business context, growth plans, and regulatory requirements to deliver actionable insights—not just a list of findings.
Whether you're preparing for a compliance certification, experiencing performance issues, seeing unexplained cost increases, or simply want assurance that your infrastructure follows best practices, an audit provides the clarity and roadmap you need.
Why Organizations Need Infrastructure Audits
Cloud environments evolve rapidly. Without periodic assessments, technical debt accumulates and risks compound silently.
Security Blind Spots
Misconfigurations, overly permissive IAM policies, unencrypted data, and exposed endpoints often go unnoticed until a breach occurs. Audits proactively identify these risks.
Performance Degradation
As applications scale, initial architecture decisions may become bottlenecks. Audits identify performance issues before they impact users.
Cost Creep
Cloud costs can spiral without visibility. Organizations typically find 20-40% savings opportunities through proper cost optimization audits.
Compliance Requirements
SOC 2, HIPAA, PCI-DSS, and GDPR require documented evidence of security controls. Audits identify gaps before certification assessments.
Technical Debt
Quick fixes, workarounds, and legacy patterns accumulate over time. Audits help prioritize technical debt reduction and modernization efforts.
Team Transitions
When key engineers leave or new leadership joins, audits provide institutional knowledge capture and baseline documentation.
Audit Domains We Cover
Our audits provide 360-degree coverage across all critical infrastructure dimensions.
Security Audit
IAM policies & permissions, network security (VPCs, security groups, NACLs), encryption at rest & in transit, secrets management, vulnerability assessment, WAF & DDoS protection.
Performance Audit
Compute rightsizing, database optimization, caching strategies, CDN configuration, auto-scaling policies, latency analysis, I/O bottlenecks, observability gaps.
Cost Optimization Audit
Unused resources, oversized instances, savings plans opportunities, storage tiering, data transfer costs, reserved capacity analysis, spot instance candidates.
Compliance Audit
SOC 2 Type II controls, HIPAA safeguards, PCI-DSS requirements, GDPR data handling, ISO 27001 alignment, audit logging, access controls, data residency.
Architecture Review
High availability design, disaster recovery capabilities, scalability patterns, microservices architecture, Kubernetes setup, service mesh, API gateway patterns.
DevOps & Automation Audit
CI/CD pipelines, Infrastructure as Code, GitOps practices, deployment strategies, environment parity, testing automation, release management.
Our Audit Process
A structured, thorough approach that combines automated tools with expert analysis.
Discovery & Scoping
Understand your environment, business objectives, and specific concerns. Define audit scope—which accounts, regions, services, and compliance frameworks to cover. Set up read-only access for our assessment tools.
Automated Assessment
Deploy industry-leading scanning tools (AWS Config, Prowler, ScoutSuite, Checkov) to perform comprehensive automated checks across hundreds of best practice benchmarks and compliance controls.
Expert Analysis
Our certified architects review automated findings, eliminate false positives, and perform deeper analysis. We examine architecture patterns, interview your team, and assess operational practices that tools can't evaluate.
Findings & Recommendations
Compile findings into a comprehensive report with severity ratings, business impact analysis, and specific remediation steps. Include architecture diagrams, cost projections, and a prioritized action plan.
Presentation & Remediation
Present findings to your team, walk through critical issues, and prioritize remediation. Optionally engage us to implement recommendations alongside your engineers or independently.
Audit Deliverables
Comprehensive documentation that drives action—not just a checklist of findings.
Executive Summary
High-level overview for leadership with risk score, key findings, cost savings potential, and strategic recommendations. Designed to communicate audit outcomes to non-technical stakeholders.
Detailed Findings Report
Comprehensive technical documentation of all findings, categorized by domain and severity (Critical/High/Medium/Low). Each finding includes evidence, business impact, and specific remediation steps.
Architecture Diagrams
Current-state and recommended target-state architecture diagrams. Visual representation of your infrastructure with annotations highlighting areas of concern and improvement opportunities.
Compliance Gap Analysis
Mapping of your current controls against required frameworks (SOC 2, HIPAA, PCI-DSS). Clear identification of gaps with specific controls needed for compliance achievement.
Cost Optimization Report
Detailed breakdown of cost saving opportunities with projected monthly and annual savings. Includes implementation effort estimates and ROI calculations for each recommendation.
Prioritized Remediation Roadmap
Action plan organized by priority, effort, and impact. Phased approach that addresses critical issues first while building toward long-term infrastructure excellence.
Common Findings We Uncover
Based on hundreds of audits, these are the issues we most frequently discover.
Overly Permissive IAM
Admin access granted broadly, service accounts with excessive permissions, missing MFA, long-lived access keys, and policies not following least-privilege principles.
Remediation
Implement role-based access control, enforce MFA, rotate credentials, use temporary credentials with IAM roles, and audit permissions regularly.
Database Bottlenecks
Missing indexes, inefficient queries, undersized instances, no read replicas, missing connection pooling, and improper caching strategies causing unnecessary database load.
Remediation
Optimize queries, implement proper indexing, add read replicas, deploy caching layers (Redis/ElastiCache), and rightsize database instances.
Resource Waste
Idle EC2 instances, oversized instances running at 5-10% utilization, unattached EBS volumes, old snapshots, unused Elastic IPs, and NAT Gateway overuse.
Remediation
Terminate unused resources, rightsize instances, implement auto-scaling, use spot instances for fault-tolerant workloads, and purchase savings plans.
Single Points of Failure
Single-AZ deployments, no auto-scaling, missing health checks, inadequate backup strategies, no disaster recovery plan, and untested failover procedures.
Remediation
Deploy across multiple AZs, implement auto-scaling, configure proper health checks, establish backup policies, and create/test DR runbooks.
Insufficient Logging
CloudTrail not enabled in all regions, no centralized log aggregation, missing VPC flow logs, inadequate log retention, and no alerting on security events.
Remediation
Enable comprehensive logging, centralize in SIEM/log management, configure appropriate retention, and set up security alerts.
Manual Operations
Infrastructure provisioned manually via console, no Infrastructure as Code, manual deployments, missing CI/CD pipelines, and undocumented configurations.
Remediation
Implement Terraform/CloudFormation for IaC, establish CI/CD pipelines, document runbooks, and automate routine operations.