Top 10 Cloud Security Providers and Solutions in 2025
- Nitin Yadav
- Knowledge
About

Discover the top cloud security companies and providers in 2025. Learn how leading vendors secure AWS, Azure & GCP with advanced cloud security solutions.
Industries
- AWS cloud security provider, Azure cloud security services, best cloud security providers, Cloud Security Companies, cloud security consulting, cloud security provider, cloud security providers 2025, Cloud Security Solutions, Google Cloud security companies, managed cloud security services, top cloud security companies
Share Via
Data security is the most significant concern with cloud computing. And if you are a business leader looking for the top cloud security software vendors but unsure which one to choose, you’ve come to the right place.
According to Cybersecurity Ventures, cybercrime is estimated to cost the world $10.5 trillion annually by 2025 a steep increase from just about $3 trillion in 2015. This staggering number highlights the reach of cyber threats. It also portrays a vivid picture of how much money organizations might lose if they don’t secure their cloud environments.
This article will explore cloud security vendors and their unique features. We will learn what sets them apart and how they may align with your business needs.
Let’s dive into understanding what a cloud security software vendor does.
What is a Cloud Security Software Vendor?
A cloud security company offers extensive services to protect your digital assets. It does more than just protect your infrastructure from insidious data breaches and safeguard backups. It also provides seamless disaster recovery solutions.
A trusted leader in cloud security will employ a set of technologies to protect all aspects of your cloud operations. Among its offerings will be:
- Network traffic filtering and encryption Cloud security companies will process your online communication.
- A unique Identity & Access Management (IAM) service
- Additional features like intelligent threat detection, incident response, and recurring risk analysis.
Safeguard your cloud environment with SquareOps‘ end-to-end cloud security solutions to protect your data, applications, and workloads.
Importance of Cloud Security

As a business leader, you must understand the need for cloud security, regardless of what industry you are in. Cloud exploitation incidents have been booming in parallel with public cloud environments growing ever more intricate as businesses transition to the cloud.
According to IBM’s Threat Landscape Report, in 99% of cases analyzed, cloud identities had excessive privileges, making misconfigurations one of the most significant risks to cloud environments. Multi-cloud configurations are complex, making it difficult for companies to implement security practices in some areas. This leaves many cracks that cybercriminals can exploit.
The increased security incidents have caused firms to increase their enterprise spending on cloud-device protection solutions. This upward trend highlights the importance of cloud security. Companies must store and secure sensitive information and safeguard consumer trust.
Organizations address these threats with more sophisticated security, such as zero-trust architectures. The whole method operates on the idea of “never rely on, always verify,” wherever each access request is established and accredited, successively decreasing the danger once it involves unauthorized entry.
Organizations prioritizing cloud security, therefore, stand to safeguard their data, retain customer confidence, and gain a competitive edge against an ever-evolving cyber threat landscape.
Evaluation Criteria for Cloud Security Companies
There are a few critical ways to assess cloud security companies. Select platforms that deliver complete multi-cloud security and monitoring. This means those platforms must be able to protect workloads on multiple cloud providers, such as AWS, Azure, or Google Cloud. This ensures the security policies for threats are consistent across all. SquareOps is an official AWS partner, for instance.
Then, select businesses that use cyber insurance and have implemented a zero-trust architecture for financial protection. All users and devices are considered untrusted until proven otherwise, drastically reducing the possibility of unauthorized access. Finally, compare the cloud security companies that offer services specific to the cloud and determine whether they support hybrid environments.
Companies need a robust third-party integration framework. If it integrates with security information and event management (SIEM) systems, such a framework can perform flawlessly across complex environments.
Now that we know what to look for, let’s explore some of the top cloud security companies.
Top Cloud Security Companies
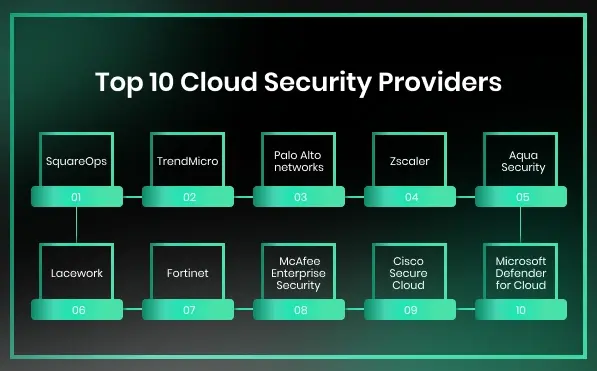
1. SquareOps
SquareOps is a leading cloud security provider that offers tailored security solutions for SaaS and product companies. We focus on securing robust cloud infrastructures across various platforms, such as AWS, Google Cloud, and Azure security.
With a full array of services, we enable scalability, security, and disaster recovery, making us ideal partners for any company looking to ensure stable cloud operations.
Key Features and Solutions:
- Application security: Keep your applications protected from SQL or XSS attacks.
- Network security: Let us keep you safe from DDoS attacks that can slow down your entire network.
Use Cases and Cybersecurity Solutions at SquareOps
We have established successful partnerships with SaaS and other product companies to secure their cloud environments in disaster recovery and serverless computing areas.
From improving security postures to maintaining performance with proactive monitoring, SquareOps provides tailored solutions for businesses migrating or enhancing their cloud infrastructure.
Don’t just take our word for it; do take a look at what our clients have to say about SquareOps:
- “Working with SquareOps was highly beneficial for our company. Their deep knowledge of DevOps and AWS technologies optimized our processes and enhanced security. Excellent communication and timely delivery. Great experience!” – Varun Arora, 2024
- “A very skilled team…we got clear deadlines with goals. Highly recommend SquareOps.” – Jesper, co-founder and CIO at Mathleaks
Learn more about our expertise and take your cloud performance and security to the next level with SquareOps advanced solutions.
2. TrendMicro
TrendMicro is another leader in providing cloud security for companies. They provide advanced threat detection and compliance management across public, private, and hybrid clouds.
Their focus on malware protection, vulnerability management, and innovative intrusion prevention systems (IPS) technology shields cloud workloads from new dangers.
Key Features:
- Malware Protection: All-inclusive security from both established and future malware.
- Cloud Vulnerability Management: Periodically scan and report vulnerabilities found inside cloud assets as they are disseminated across the internet.
- IPS (Intrusion Prevention System): This system monitors networks and/or systems for malicious or unwanted activity and takes action if it detects it.
- Compliance Reporting: Provides automated reporting and alerts to make compliance easier.
3.Palo Alto Networks
Palo Alto Networks is famous for its Prisma Cloud platform, which provides cybersecurity solutions across cloud applications, data, and workloads.
They also offer cloud-native security, threat detection, and compliance solutions built from the ground up to secure multi-cloud and hybrid environments end-to-end against vulnerabilities.
Key Features:
- Cloud-Native Security: Secures applications, data, and workloads built for the cloud.
- Protection: Instant protection against threats using native cloud detection instruments.
- Audit and Compliance: Continuous compliance monitoring and reporting.
- Security: Comprehensive multi-cloud data security.
- Vulnerability Management: Detects & Patches vulnerabilities within the cloud workloads.
4. Zscaler
Zscaler’s zero-trust exchange platform is worth noting as it helps safeguard internet traffic and protects users, devices, and applications against cyber threats. Interestingly, they offer a zero-trust environment, meaning only authenticated users are allowed inside the network. Such a design dramatically reduces the chances of unauthorized access, which can be beneficial for your organization.
Key Features:
- Threat Intelligence: Identify and respond to threats as they occur.
- Application Security: An added layer of security to protect cloud applications from cyber threats.
- Drives Encrypted Traffic Inspection: This allows for the re-direction of all traffic from remote locations through a third-party processing device, allowing user inspection and control.
- Secure Internet and SaaS Access: Eases the ability to connect securely to cloud applications.
5. Aqua Security
Moving on to Aqua Security, which offers vulnerability assessment and runtime security compliance services. These services ensure that containerized workloads and serverless environments are secure so companies can safely use cloud technology.
Key Features:
- Container Security: Offers real-time security for containerized applications.
- Vulnerability Assessment: Detects security issues in your container images before deployment.
- Runtime Security Compliance: Watches container behavior and ensures nothing fishy is happening.
- Serverless Security: A security to protect serverless functions from malicious actions.
- Policy-Based Controls: Automated implementation of security policies in containerization environments.
6. Lacework
Lastly, Lacework provides automated cloud security through the Polygraph Platform. Their model gears them towards automation and machine learning. They monitor the cloud environment for possible weaknesses and abnormal activities.
Key Features:
- Anomaly Detection: It uses machine learning to detect abnormal patterns.
- IT Compliance Reporting: Compliance tracking and reporting automated through AI.
- Threat Intelligence: This delivers contextualized threat intelligence to rapid response.
- Protection of Workloads: Monitor your cloud-based workloads for constant risks to safety.
- Visibility & Context: Provides unmatched visibility and context into cloud activity.
7. Fortinet
Offers network and application-level security solutions.
Scalable firewalls and intrusion detection.
Popular with enterprises needing integrated security stacks.
Best for: Enterprises scaling both networks and applications.
8. McAfee Enterprise Security
Provides SaaS security and malware prevention.
Known for cloud threat defense and antivirus capabilities.
Evolving to support enterprise cloud-first environments.
Best for: Organizations needing classic security + cloud updates.
9. Cisco Secure Cloud
Secure networking combined with cloud-first solutions.
Focus on enterprise connectivity and workload defense.
Backed by Cisco’s global reputation in IT.
Best for: Enterprises already invested in Cisco infrastructure.
10. Microsoft Defender for Cloud
Native to Azure, but extends to AWS and GCP.
Unified visibility for workloads across providers.
Strong compliance integration for enterprise users.
Best for: Azure-heavy enterprises with multi-cloud needs.
Innovations in Cloud Security Solutions
As cloud architecture grows more sophisticated, organizations have started employing practices such as Cloud Security Posture Management (CSPM) and Infrastructure as Code (IaC) to improve security.
CSPM eliminates misconfigurations, security risks, and compliance violations across different cloud environments as an automated tool.
This preventative strategy guarantees that cloud assets are firmly secured in adherence to the accepted best practices.
By employing IaC, security policies can be built into the development stages, minimizing the risk of having to enforce them at later stages. This, in turn, allows security procedures to be incorporated during the development process.
Thus, it reduces human error and improves the security of the infrastructure.
In addition, many businesses focus on Cloud-Native Application Protection Platforms (CNAPP). It provides robust, integrated security solutions to protect applications, workloads, and data throughout the cloud.
All-in-one CNAPP platforms can perform multiple security tasks, including workload protection and network duties. Combined with behavioral detection, they instantly identify threats and respond immediately to them and their exposure.
These advances are essential for companies aiming for the best protection and compliance in the cloud. They help minimize risk in a dynamic cloud configuration in the current scenario.
Key Features of Cloud Security Solutions

Cloud security solutions have essential parts that assist establishments in protecting their data and operations. One of the core functions is controlling and visibility into all applications and IT environments. It allows organizations to secure their cloud infrastructure effectively.
Such a feature guarantees that unauthorized access or suspicious activities are identified and contained early to mitigate risks.
Using robust encryption also helps secure data when it is stored and transmitted.

Encryption converts texts using a cloud security policy to prevent the leakage of sensitive documents, materials, or information.
Also, any cloud security breach must adhere to specific compliance requirements, such as GDPR or HIPAA. Failure to comply with these standards may lead to adverse legal troubles and reputational damage for the companies.
Challenges in Cloud Security
Cloud security comes with innumerable benefits, but there are also a few challenges in adopting it, such as:
- Frequent updation: Organizations must keep cloud configurations up-to-date and operational to secure them. One of the biggest challenges is addressing security risks such as ransomware, which also keeps updating to get past standard security measures.
- Visibility and Control: Cloud environments are complex and dynamic, making it difficult to maintain visibility and control over resources. This can lead to misconfigurations and security gaps.
- Skilled Maintenance: Maintaining instances on the cloud is not particularly easy, as there are so many variables that can affect security and maintenance. Luckily, experts like SquareOps can help you sort this out.
By overcoming these challenges and implementing robust cloud security solutions, businesses can protect their digital assets and effectively safeguard trust.
Final Thoughts
Defending a business’s digital assets in today’s Digital space requires stringent cloud security. Given the increasing complexity of cloud environments and rising threat levels, security is no longer optional but necessary.
The proper security measures, from data encryption to multi-cloud monitoring, will keep your cloud infrastructure strong while giving you peace of mind that it is secure.
Just as technology progresses, cybercriminals’ techniques evolve, too. Security systems must develop, update, and evaluate themselves constantly and regularly, or they will never stay ahead of potential threats.
Businesses can use advanced security solutions to ensure the security of their sensitive information in the cloud while remaining compliant with industry standards.
SquareOps is ahead of its competitors, providing custom cloud security services for product and SaaS companies. Our managed Kubernetes and Atmosly deliver integrated, scalable security, so your cloud is always performant and secure.
For the best in cloud security services, contact us today and let SquareOps protect your digital tomorrow.
Frequently asked questions
A cloud security provider is a company that offers tools, services, and managed solutions to protect workloads in AWS, Azure, GCP, and other cloud environments. They ensure compliance, prevent breaches, and provide 24/7 monitoring.
Cloud security is crucial to safeguard sensitive data, maintain regulatory compliance, and protect the organization’s reputation.
Common challenges include data breaches, unauthorized access, misconfigurations, insider threats, and lack of visibility into cloud environments.
Leading cloud security companies include SquareOps, Trend Micro, ZScaler, Palo Alto Networks, and Trend Micro.
Key solutions include Cloud Access Security Broker (CASB), Cloud Security Posture Management (CSPM), Cloud Workload Protection Platform (CWPP), Data Loss Prevention (DLP), and encryption.
When selecting a solution, consider factors like your organization’s specific needs, budget, and the complexity of your cloud environment.
Best practices include implementing strong access controls, regularly patching systems, conducting security assessments, enforcing data encryption, monitoring cloud activities, and educating employees.
To stay informed, follow industry news, read our blogs, check out popular online forums, and consult with cybersecurity experts like SquareOps!
Related Posts
Comprehensive Guide to HTTP Errors in DevOps: Causes, Scenarios, and Troubleshooting Steps
- Blog

Trivy: The Ultimate Open-Source Tool for Container Vulnerability Scanning and SBOM Generation
- Blog

Prometheus and Grafana Explained: Monitoring and Visualizing Kubernetes Metrics Like a Pro
- Blog

CI/CD Pipeline Failures Explained: Key Debugging Techniques to Resolve Build and Deployment Issues
- Blog

DevSecOps in Action: A Complete Guide to Secure CI/CD Workflows
- Blog

AWS WAF Explained: Protect Your APIs with Smart Rate Limiting
- Blog

