What Is a Cloud Operations Maturity Model?
A cloud operations maturity model is a framework that helps organizations assess how well they manage their cloud infrastructure—from provisioning and monitoring to security, cost control, and incident response. It defines clear stages of operational capability so you can identify where you are today and what specific improvements will move you forward.
Most organizations overestimate their cloud maturity. They've adopted AWS or GCP, set up a few pipelines, and assume they're "cloud-native." But when an incident hits at 2 AM, when the monthly bill spikes 40% without explanation, or when a single engineer leaving causes knowledge gaps across the entire infrastructure—that's when the gaps become painfully visible.
This guide breaks down the five stages of cloud operations maturity, gives you a self-assessment framework, and provides actionable steps to advance from each level to the next.
Why Cloud Operations Maturity Matters in 2026
Cloud spending continues to grow, but so does cloud waste. According to Flexera's 2025 State of the Cloud report, organizations estimate 28% of cloud spend is wasted. At the same time, the complexity of modern cloud environments—multi-account architectures, Kubernetes clusters, serverless workloads, hybrid setups—demands operational discipline that most teams haven't built yet.
Cloud operations maturity directly impacts:
- Incident response speed: Mature teams detect and resolve issues in minutes. Immature teams learn about outages from customers.
- Cost predictability: Mature organizations can forecast cloud spend within 5%. Immature ones get monthly bill surprises.
- Engineering velocity: Mature platforms enable self-service provisioning in minutes. Immature ones create weeks-long ticket queues.
- Security posture: Mature teams enforce policy-as-code and automated compliance. Immature ones rely on manual audits that happen quarterly at best.
- Talent retention: Engineers leave organizations where they spend more time firefighting than building.
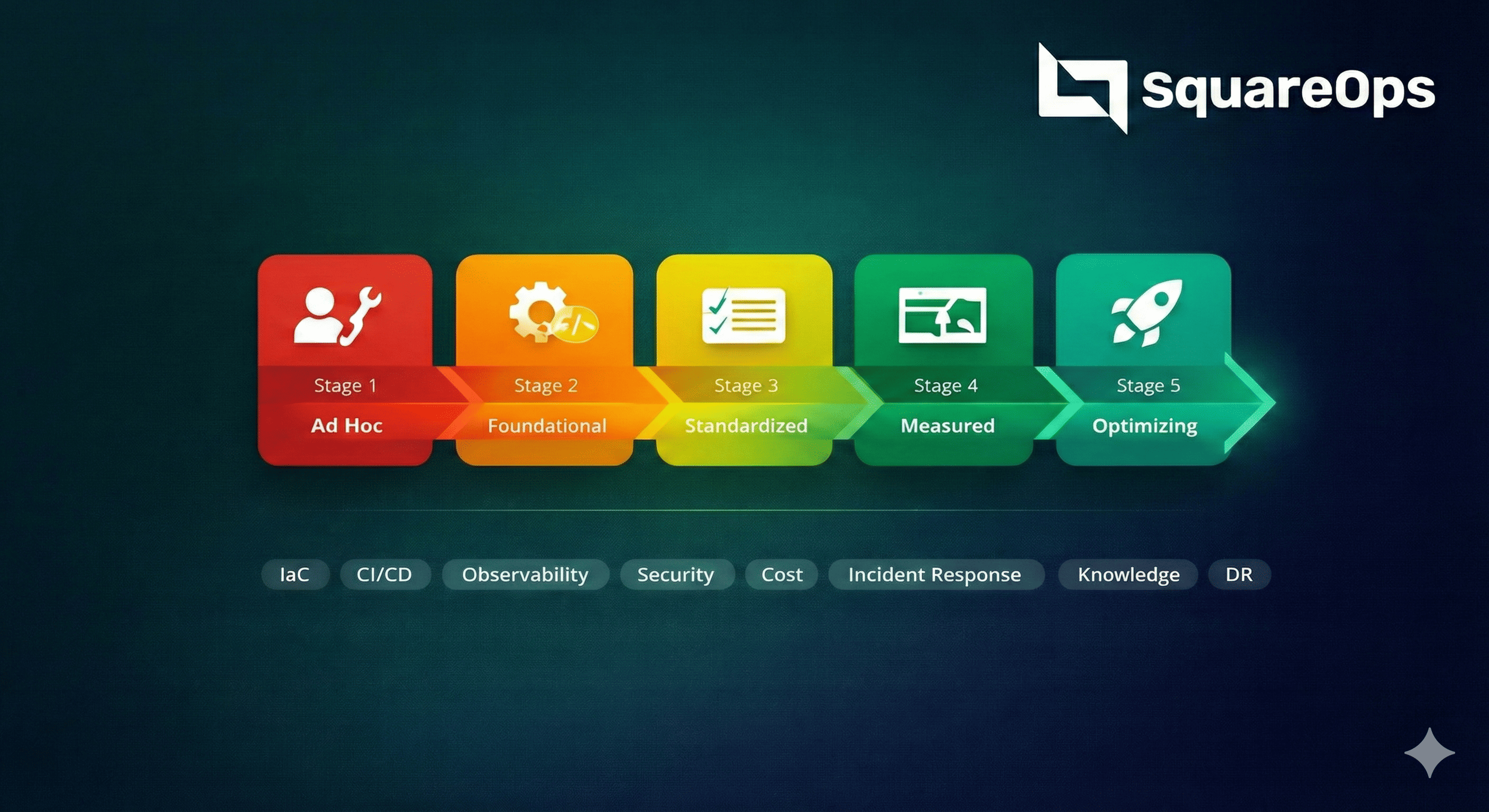
The Five Stages of Cloud Operations Maturity
Stage 1: Ad Hoc (Manual and Reactive)
Characteristics:
- Infrastructure is provisioned manually through the AWS/GCP/Azure console
- No Infrastructure as Code—changes are made by clicking through UIs
- Monitoring is limited to basic CloudWatch dashboards that nobody checks regularly
- No defined incident response process; engineers scramble when something breaks
- Secrets are stored in environment variables, config files, or (worst case) committed to Git
- Cost management means looking at the bill when it arrives and being surprised
- One or two people hold all infrastructure knowledge in their heads
Typical signs: "Only DevOps person knows how to deploy." "We don't know why our bill went up." "It works on my machine."
Common at: Early-stage startups, small teams with no dedicated DevOps/platform engineering role.
Stage 2: Foundational (Basic Automation)
Characteristics:
- Some infrastructure is managed with Terraform or CloudFormation, but not all
- CI/CD pipelines exist for application deployments but infrastructure changes are still partially manual
- Basic monitoring and alerting in place—CPU, memory, disk alerts fire but often get ignored
- Secrets have moved to SSM Parameter Store or Secrets Manager, at least for production
- A tagging strategy exists on paper but isn't enforced consistently
- Incident response is ad hoc but documented post-mortems have started
- Single AWS account or poorly structured multi-account setup
Typical signs: "We have Terraform but it doesn't cover everything." "Alerts fire but we're not sure which ones matter." "Our staging environment doesn't match production."
Common at: Series A/B startups, growing teams that just hired their first platform/DevOps engineer.
Stage 3: Standardized (Consistent and Documented)
Characteristics:
- All infrastructure is managed via IaC—no manual console changes in production
- CI/CD covers both application and infrastructure deployments with proper approval gates
- Observability stack includes metrics, logs, and traces with meaningful alert thresholds
- AWS Organizations with proper multi-account structure (workload, security, logging, shared services)
- IAM follows least-privilege with regular access reviews
- Cost allocation tags are enforced via SCPs and AWS Config rules
- Incident response runbooks exist for common failure scenarios
- Disaster recovery is documented with defined RTO/RPO targets (but may not be regularly tested)
- Platform team provides reusable modules and golden paths for common workloads
Typical signs: "Everything is in Terraform." "We have runbooks for the common issues." "We know our cost breakdown by team and environment."
Common at: Scale-ups, Series C+ companies, mid-market enterprises with dedicated platform teams.
Stage 4: Measured (Data-Driven Operations)
Characteristics:
- SLOs (Service Level Objectives) and error budgets are defined and tracked for all critical services
- SRE practices are adopted—toil is measured and systematically reduced
- Full DevSecOps pipeline: security scanning (SAST, DAST, container scanning) integrated into CI/CD
- Automated compliance checks run continuously (AWS Config, Security Hub, custom policy-as-code)
- Cost optimization is proactive: right-sizing recommendations are acted on monthly, Savings Plans are reviewed quarterly
- Chaos engineering or game days are conducted to validate resilience
- Self-service platform: development teams can provision approved resources without waiting for the platform team
- Deployment frequency is measured and continuously improved
- MTTR (Mean Time to Recovery) is tracked and improving quarter over quarter
Typical signs: "We track MTTR and deployment frequency." "Our error budget determines feature vs reliability work." "Developers provision their own environments through our internal platform."
Common at: Mature tech companies, enterprises with established SRE/platform engineering organizations.
Stage 5: Optimizing (Continuous Improvement and Innovation)
Characteristics:
- Internal Developer Platform (IDP) with full self-service, guardrails built into the platform itself
- AI/ML-assisted operations: anomaly detection, predictive auto-scaling, automated remediation
- FinOps is a core practice: unit economics (cost per customer, cost per transaction) drive architectural decisions
- Multi-cloud or hybrid strategy is intentional and well-managed (not accidental sprawl)
- Zero-trust security model is fully implemented across network, identity, and workload layers
- Compliance is continuous and automated—audit preparation takes hours, not weeks
- Infrastructure decisions are driven by business metrics, not just technical metrics
- The platform team operates as an internal product team with SLAs to their internal customers
- Knowledge sharing is systematic: architecture decision records (ADRs), internal tech radar, regular tech talks
Typical signs: "We measure cost per customer and optimize architectures around business outcomes." "Our platform team has an internal NPS score." "Compliance audits are a non-event."
Common at: Cloud-native technology companies, enterprises that have invested heavily in platform engineering for 3+ years.
Self-Assessment: Where Does Your Organization Stand?
Rate your organization on each dimension below from 1 (Ad Hoc) to 5 (Optimizing). Be honest—the goal is to identify gaps, not to score well.
| Dimension | 1 - Ad Hoc | 3 - Standardized | 5 - Optimizing |
|---|---|---|---|
| Infrastructure Provisioning | Manual console clicks | 100% IaC with modules | Self-service IDP with guardrails |
| CI/CD | Manual deployments or basic scripts | Automated pipelines with approval gates | Progressive delivery (canary, blue-green) with auto-rollback |
| Observability | Basic CPU/memory alerts | Metrics, logs, traces with SLO dashboards | AI-driven anomaly detection and auto-remediation |
| Security | Manual reviews, overly permissive IAM | Policy-as-code, automated scanning in CI/CD | Zero-trust, continuous compliance, automated audit |
| Cost Management | Reactive bill review | Tags enforced, cost allocated by team/project | Unit economics drive architecture decisions |
| Incident Response | Ad hoc firefighting | Runbooks, defined on-call, blameless post-mortems | SLOs, error budgets, chaos engineering, automated remediation |
| Knowledge Management | Tribal knowledge in one person's head | Documented runbooks and architecture diagrams | ADRs, tech radar, systematic knowledge sharing |
| Disaster Recovery | No DR plan | Documented RTO/RPO, tested annually | Automated failover, tested quarterly via game days |
Scoring:
- 8–16: Stage 1–2 (Ad Hoc / Foundational) — Focus on building the basics
- 17–24: Stage 2–3 (Foundational / Standardized) — Focus on consistency and standards
- 25–32: Stage 3–4 (Standardized / Measured) — Focus on metrics-driven operations
- 33–40: Stage 4–5 (Measured / Optimizing) — Focus on continuous improvement and innovation
How to Advance from Each Stage
Stage 1 → Stage 2: Build the Foundation
This is the highest-ROI transition. Small investments here eliminate entire categories of risk.
- Adopt Terraform for all new infrastructure. Don't try to import everything at once—start with new resources and gradually import existing ones.
- Set up a basic CI/CD pipeline for your most critical application. Even a simple GitHub Actions or GitLab CI workflow that builds, tests, and deploys is a massive improvement over manual deployments.
- Move secrets to AWS Secrets Manager or SSM Parameter Store. This is a one-time effort that permanently eliminates a major security risk.
- Implement basic monitoring: CloudWatch alarms for CPU, memory, disk, and HTTP 5xx errors. Route alerts to Slack or PagerDuty. Even imperfect alerting is infinitely better than none.
- Document your infrastructure. Start with a simple architecture diagram and a list of all AWS accounts, VPCs, and critical services.
Stage 2 → Stage 3: Standardize Everything
The goal here is consistency. Every environment, every deployment, every alert should follow the same patterns.
- Complete your IaC coverage to 100%. Use
terraform importfor existing resources. Set up an SCP that blocks console-created resources in production accounts. - Structure your AWS accounts using AWS Organizations: separate accounts for workloads, security, logging, and shared services.
- Build reusable Terraform modules for common patterns (VPC, EKS cluster, RDS, ALB). Publish them in an internal registry. SquareOps maintains open-source Terraform modules you can use as starting points.
- Upgrade your observability from basic alerting to a full stack: Prometheus + Grafana for metrics, centralized logging with CloudWatch Logs or ELK, and distributed tracing with OpenTelemetry.
- Enforce tagging using AWS Organizations Tag Policies and implement cost allocation so every dollar is attributed to a team and environment.
- Write incident response runbooks for your top 10 most common failure scenarios. Start conducting blameless post-mortems after every incident.
Stage 3 → Stage 4: Measure and Optimize
You have the foundation. Now add the feedback loops that drive continuous improvement.
- Define SLOs for every customer-facing service. Start with availability (e.g., 99.9%) and latency (e.g., p95 < 200ms). Track error budgets monthly.
- Adopt SRE practices: measure toil, set toil reduction targets, and fund reliability work through error budget policies.
- Integrate security into CI/CD with DevSecOps: container image scanning (Trivy), SAST (Semgrep), dependency scanning, and IaC security scanning (Checkov/tfsec).
- Implement a self-service platform so developers can provision approved resources (databases, caches, queues) through a portal or CLI without filing tickets.
- Track DORA metrics: deployment frequency, lead time for changes, change failure rate, MTTR. Use these to identify bottlenecks in your delivery pipeline.
- Start chaos engineering. Begin with simple experiments: terminate a random pod, failover a database, simulate an AZ outage. Use the results to improve resilience.
Stage 4 → Stage 5: Optimize Continuously
- Build or adopt an Internal Developer Platform (IDP) with Backstage or a custom solution. Encode all guardrails (security, cost, compliance) into the platform itself.
- Adopt FinOps as a practice. Move beyond cost allocation to unit economics—measure cost per customer, cost per API call, cost per transaction. Let business metrics drive architecture decisions.
- Implement continuous compliance using policy-as-code frameworks (OPA/Rego, AWS Config rules, custom Lambda-backed rules). Compliance should be verified every hour, not every quarter.
- Invest in AIOps: anomaly detection on metrics and logs, predictive auto-scaling, automated runbook execution for known failure patterns.
- Treat your platform team as a product team: gather feedback from internal customers, track adoption metrics, maintain an internal SLA, and iterate based on data.
Common Maturity Advancement Pitfalls
- Skipping stages: You can't implement SLOs (Stage 4) without reliable observability (Stage 3). Each stage builds on the previous one. Trying to jump ahead creates a fragile facade of maturity.
- Tool-first thinking: Buying Datadog doesn't make you mature at observability. Adopting Terraform doesn't make you mature at IaC. Tools are enablers, but maturity comes from processes, practices, and culture.
- Ignoring the people dimension: Cloud maturity isn't purely technical. It requires organizational changes—on-call culture, blameless post-mortems, cross-functional collaboration, knowledge sharing.
- Boiling the ocean: Don't try to advance on all 8 dimensions simultaneously. Pick the 2–3 dimensions with the highest business impact and focus there first.
- Not measuring progress: If you can't measure it, you can't improve it. Set specific, time-bound goals for each dimension (e.g., "100% IaC coverage by Q2" or "MTTR under 30 minutes by Q3").
Recommended Maturity Targets by Company Stage
| Company Stage | Target Maturity Level | Priority Dimensions |
|---|---|---|
| Pre-Seed / Seed | Stage 1–2 | Basic CI/CD, IaC for core infra, secrets management |
| Series A | Stage 2–3 | Full IaC, monitoring/alerting, multi-account structure, cost tagging |
| Series B/C | Stage 3 | Standardized everything, incident response, DR planning, DevSecOps basics |
| Growth / Late Stage | Stage 3–4 | SLOs, SRE practices, self-service platform, DORA metrics |
| Enterprise | Stage 4–5 | FinOps, continuous compliance, IDP, chaos engineering |
Being at Stage 2 as a seed-stage startup is perfectly appropriate. Being at Stage 2 as a Series C company processing financial transactions is a serious risk. Context matters.
How SquareOps Helps Organizations Advance Their Cloud Maturity
At SquareOps, we've helped organizations at every stage of cloud maturity build the practices, platforms, and automation they need to operate reliably at scale. Our approach includes:
- Cloud Operations Maturity Assessment: We evaluate your current state across all 8 dimensions and deliver a prioritized roadmap with specific, actionable recommendations.
- DevOps and Platform Engineering: We build and manage your CI/CD pipelines, IaC modules, observability stack, and self-service platform so your engineering team can focus on product.
- Site Reliability Engineering: We implement SLOs, error budgets, on-call practices, and chaos engineering to drive measurable reliability improvements.
- FinOps and Cost Optimization: We implement cost allocation, right-sizing, Savings Plans optimization, and unit economics tracking. Typical clients reduce cloud spend by 30–50%.
- Cloud Security and Compliance: We implement policy-as-code, automated compliance checks, and SOC 2 / PCI DSS readiness programs.
Whether you're a startup building your first cloud foundation or an enterprise optimizing a complex multi-account environment—talk to us about a cloud maturity assessment. We'll give you a clear picture of where you stand and a concrete plan to get where you need to be.