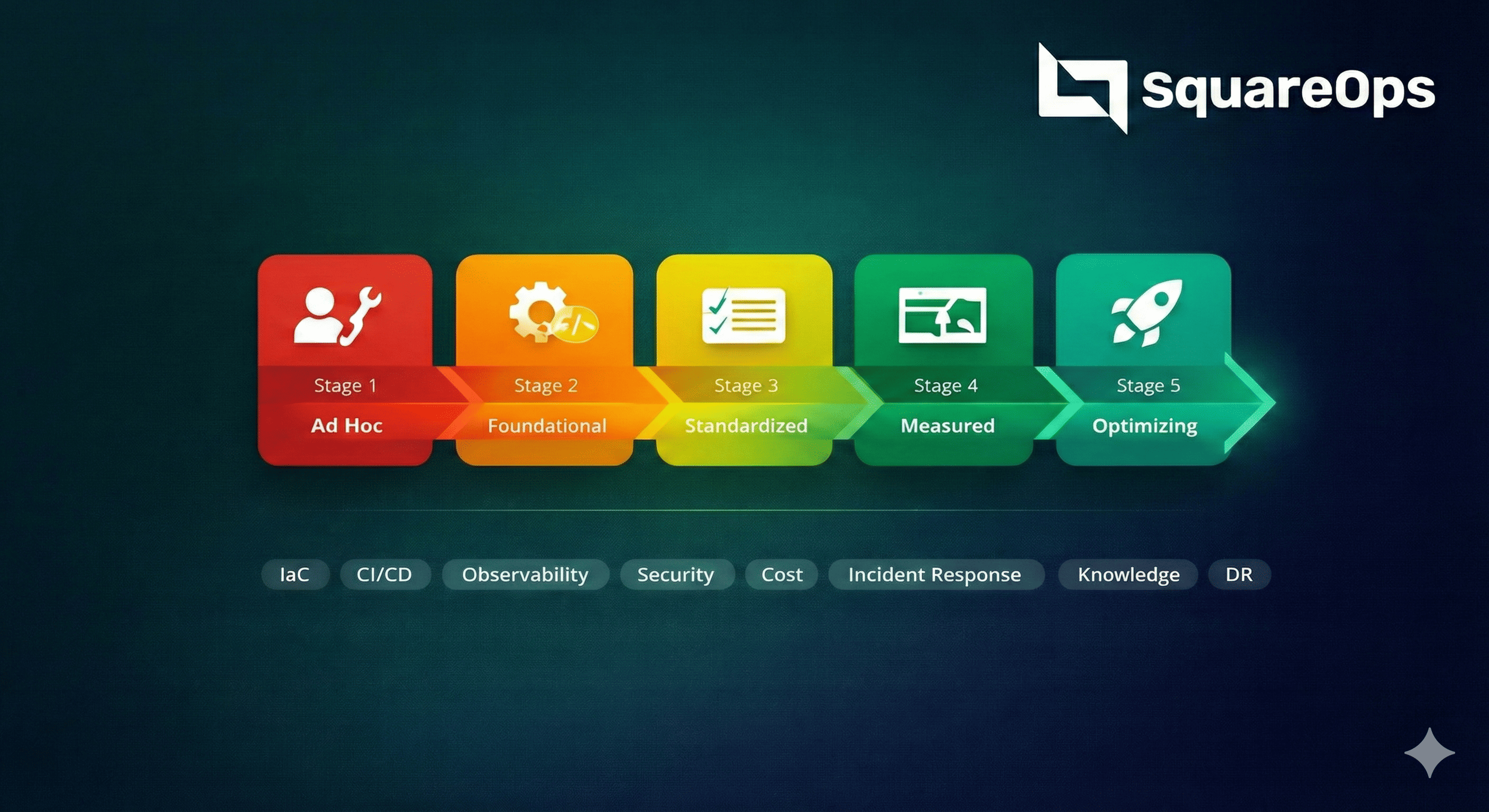
Cloud Operations Maturity Model: Where Your Organization Stands & How to Improve
Assess your cloud operations maturity across 8 dimensions—from ad hoc manual setups to fully optimized platforms. Learn exactly where your organization stands and get actionable steps to advance to the next level.