CIMET DevSecOps : AWS Codepipeline Case Study
- Ankush Madaan
- Case Studies
About
CIMET provides a full end-to-end digital comparison platform, using an automated system to reduce conversion times & Boost brand value and SquareOps Helped them achieve DevSecOps for the entire Infrastructure.
Industries
- AWS, CI/CD Pipelines, DevSecOps, Security
Share Via
About CIMET
CIMET provides a full end-to-end digital comparison platform, using an automated system to reduce conversion times & Boost brand value. It Help customers compare switch & save to provide better overall value
Problem Statement
As the company struggled on implementing DevOps Best Practices & Especially Security on the infrastructure, data and application, we had to provide the correct security levels for their cloud workload. This included:
- Provide centralised security across the group of application servers
- Data encryption at rest and in transit
- Introduce cybersecurity process from the beginning of development cycle
- Secure way to inject Environment variables in the application and also any other sensitive information
- Compatibility with CIS Compliance Best Practices Introduce DevSecOps concepts for Continuous Security Posture of the application and cloud infrastructure
Solution Implemented
- Solution was Implemented using AWS services and application deployment was deployed over Ec2 instances with Auto-Scaling enabled. Ec2 service was preferred over other services owing to developers familiarity with existing AWS services and to keep the setup simple. Best practices in terms of AWS Well-Architected principles were used to provide coverage on all fronts especially focusing on Security measure.
- All communication between Different Services were secured and Data at rest was also encrypted using AWS KMS to follow the strict data governance standards.The KMS Key usage permission has been granted only to the required IAM Roles and Policies and Similarly the connectivity to Database was over secure protocol.
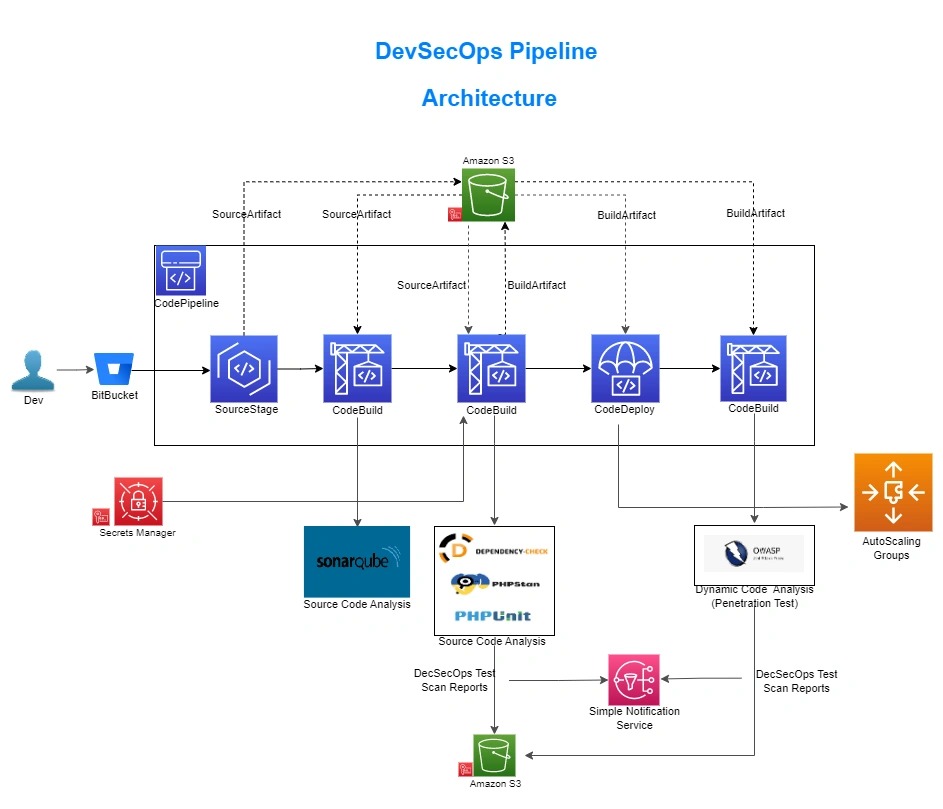
- Implementing DevSecOps was one of the critical components in achieving a continuous security posture within the pipelines. AWS CodePipeline was used, and the following tools were implemented:
- SonarQube
- Owasp Dependency Check
- Phpstan Test (SAST)
- Phpunit Test (Unit Testing)
- Owasp Zap Test (Penetration testing of Application)
- To store all the environmental variables used by the application, we have implemented Secrets Manager. The secrets are encrypted using AWS KMS keys and the key usage permission has been granted to the CodeBuild service roles and EC2 SSM roles. During the build stage, the secrets are fetched and deployed with the BuildArtifact to the target instances.
- Custom AMIs for the application have been created, with required softwares installed and maximum measures followed for CIS Compliance Compatibility. AWS Security Hub and AWS Inspector’s output reports are followed from time to time to maintain the Best Security Measures.
Results
- Maximum Security has been achieved keeping the AWS Well-architected Principles in place with the use of AWS Services like KMS, Security Hub, CloudTrail and many more.
- As only the IAM Users with restricted access could reach the resources, hence adding more security to the infrastructure.
- The newly identified security vulnerabilities get quickly managed and patched into the release cycle with the use of DevSecOps tools.
- With the use of Secrets Manager, the critical environment variables are no more part of the code. Also there is no more need to embed them in source code.
Related Posts

Smooth Migration of MongoDB & Elasticsearch to AWS
- Case Studies
BatchService cut cloud costs by 27%, improved query performance by 30%, and ensured zero downtime by migrating 12+ TB of data to AWS EKS with SquareOps’ expert-led solution.

Streamlining Deployments for Loconav with Automation
- Case Studies
SquareOps streamlined Loconav’s global deployments by automating infrastructure with Kubernetes, Terraform, and Ansible, reducing errors, costs, and deployment time from days to hours. 🚀

Scaling DevOps & Performance for MobileSentrix
- Case Studies
SquareOps streamlined Loconav’s global deployments by automating infrastructure with Kubernetes, Terraform, and Ansible, reducing errors, costs, and deployment time from days to hours. 🚀

Migration of MongoDB & Elasticsearch to AWS
- Case Studies
SquareOps helped BatchService migrate 12TB+ of MongoDB & Elasticsearch to AWS, reducing costs by 27%, improving scalability, security, and performance with a zero-downtime strategy.

AWS Control Tower Strategy For EyeControl
- Case Studies
Learn how SquareOps utilized AWS Control Tower to enhance EyeControl’s multi-account management in healthcare technology, ensuring strong security.

Transforming AWS Security Landscape For Synaptic
- Case Studies
Learn how Synaptic enhanced AWS security with SquareOps, achieving ISO27001 compliance and improved threat detection. Secure your data and empower growth with SquareOps.

